
- Web3 project Munchables on the Blast network suffered an attack.
- Investigations suggested that the attack was due to North Korean hackers.
On the 26th of March, Web3 project and crypto game Munchables suffered a loss of approximately $62.5 million in Ethereum [ETH]. This loss occurred due to the manipulation of a contract associated with the project.
Disaster recovery
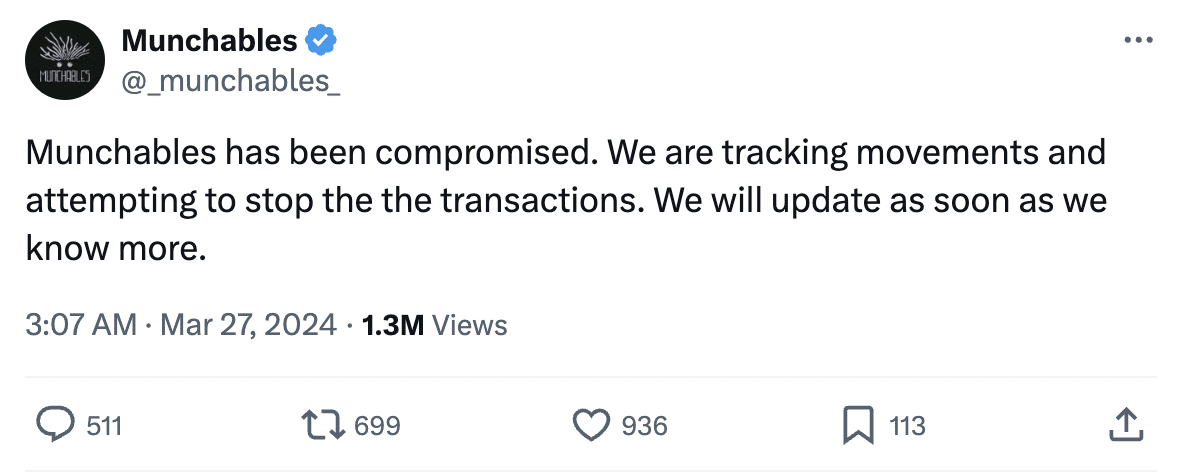
Munchables acknowledged the compromise in an X (formerly Twitter) post at 9:33 pm UTC. They confirmed they were tracking the hacker’s movements and attempting to halt the transactions.
Blockchain analyst ZachXBT identified a wallet address allegedly belonging to the attacker. This address, according to DeBank data, interacted with the Munchables protocol, siphoning off a total of 17,413 ETH.
The stolen funds were then laundered through the Orbiter Bridge, converting the Blast ETH back to standard Ethereum before being further distributed to other wallets.
Source: X
ZachXBT alleged that the culprit could be a North Korean developer with the alias “Werewolves0943,” who was hired by the Munchables team.
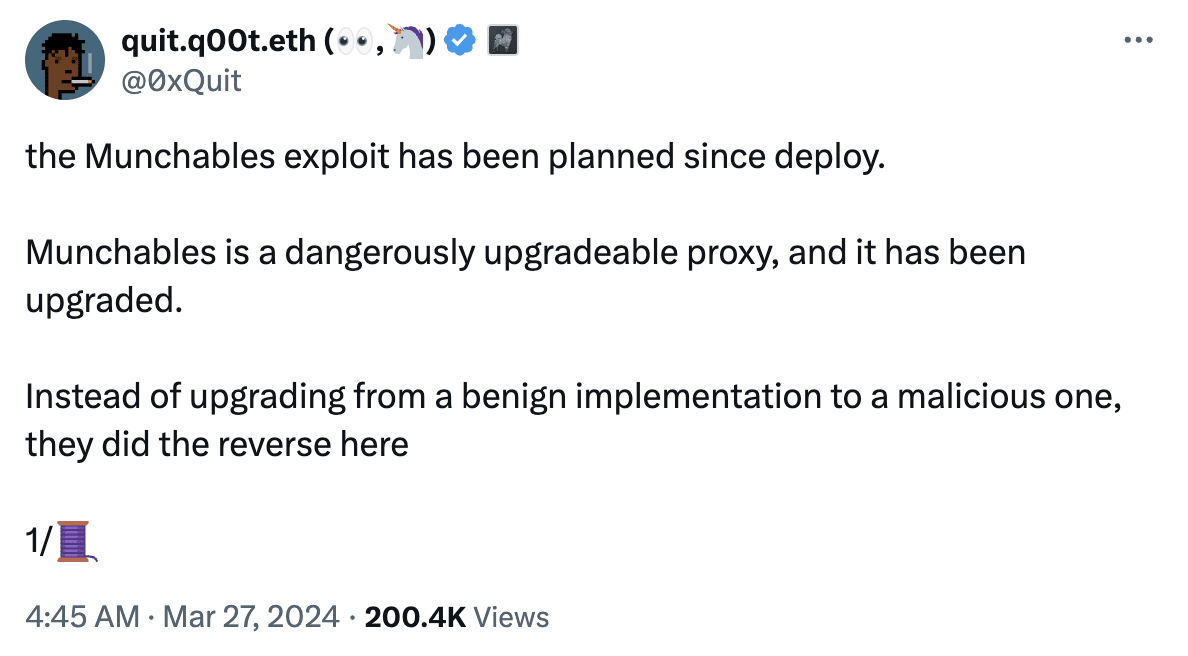
However, another X post, this time on the 27th of March, painted a more sinister picture. According to Solidity developer 0xQuit, the exploit was meticulously planned.
They pointed to a Munchables developer who upgraded the Lock contract which was designed to hold tokens for a set period with a new version shortly before launch.
According to 0xQuit, safeguards were in place to prevent withdrawals exceeding deposits.
Before the upgrade, the attacker manipulated storage slots to inflate their deposited balance to a staggering 1 million ETH.
Moreover, 0xQuit also stated that the attacker likely used manual manipulation to assign themselves this enormous balance before swapping the contract for a seemingly legitimate version.
Once the project’s TVL (total value locked) grew attractive, they simply withdrew the inflated balance.
Source: X
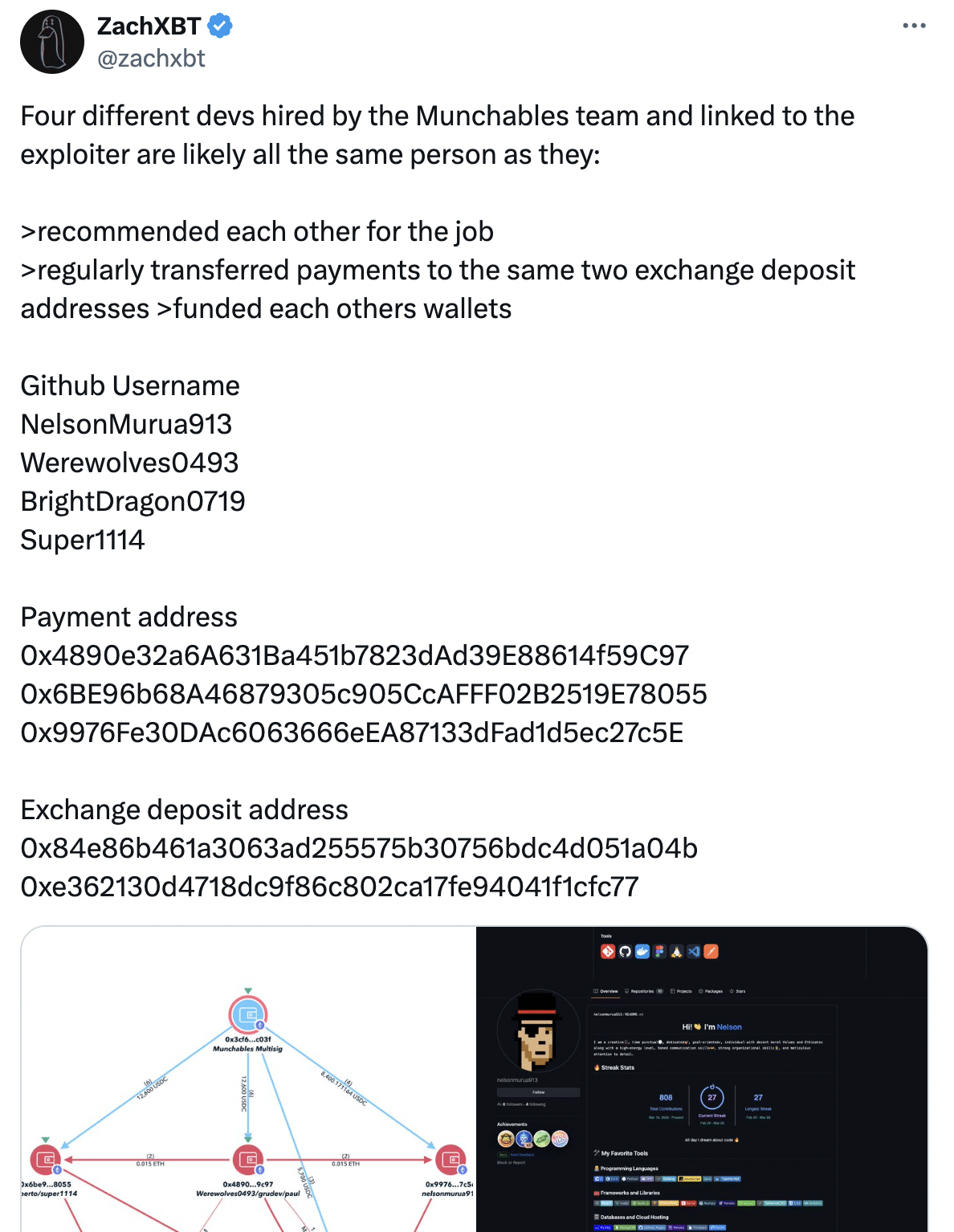
However, ZachXBT’s further investigation unearthed a connection between four developers hired by Munchables and potentially linked to the exploit.
These individuals seemingly recommended each other for the job, shared exchange deposit addresses for payments, and even funded each other’s wallets, suggesting a single actor operating under multiple aliases.
This isn’t the first crypto rodeo for North Korean hackers, as they have been involved with other attacks in the past as well.
Source: X
Impact on Blast
In the wake of this attack, the Blast community was divided. Several X users have urged the Blast team to intervene by forcibly rolling back the blockchain to a point before the exploit.
This proposal, however, faced opposition from others who argue such centralized intervention undermines the core principles of decentralized networks.
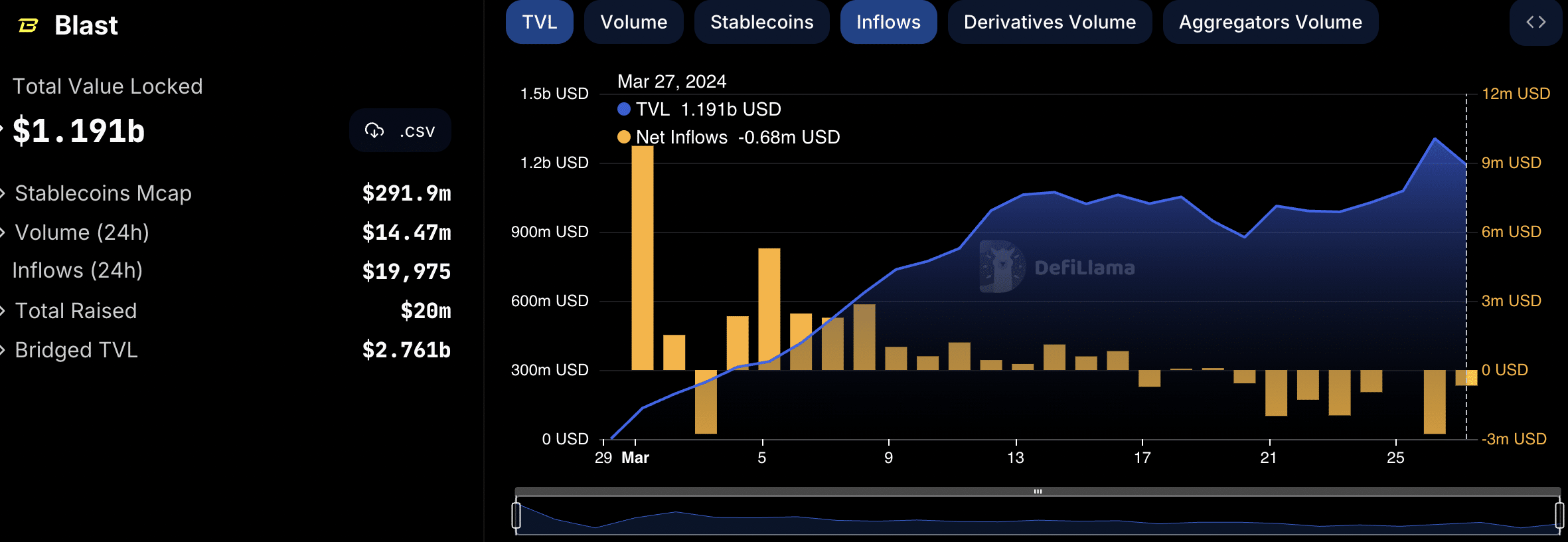
Due to these events, the outflows on Blast surged. Moreover, the TVL of the protocol also experienced a slight dip. It thus remains to be seen whether this exploit will have a significant impact on the Blast network.
Source: DeFiLlama
Powered by WPeMatico



